Bringing Real-Time Defense to Post-Deployment Open Source Software
Ortelius uses a digital twin to detect vulenrabiliites in live systems.
Digital Twins for Software Security: A New Paradigm in Post-Deployment Defense
Bringing Real-Time Defense to Post-Deployment Open Source Software
Software doesn’t stand still. Containers are rebuilt daily, services are redeployed continuously, and dependencies change faster than most security tools can track. Yet many security programs still rely on pre-deployment scans and static snapshots to manage risk.
The Ortelius project takes a different approach: post-deployment security through a software digital twin.
A digital twin gives teams a continuously updated view of what CVEs are actually running versus what was scanned last week.
What Is a Digital Twin in Software Security?
Modern software systems are increasingly distributed, dynamic, and rapidly evolving. Containers, clusters, serverless functions, and microservices move fast — but traditional security tooling struggles to keep pace. Teams need better visibility into what’s actually running in production, and they need it in real time.
That’s where the concept of a digital twin becomes mission-critical for secure software delivery. Originally popularized in aerospace and industrial engineering, digital twins are now emerging as foundational technology for modern cybersecurity and DevSecOps.
A digital twin is a living, data-driven mirror of your running software environment. Unlike static dashboards or periodic scans, a twin doesn’t represent what should be deployed — it reflects what is deployed right now. It continuously maps every component, dependency, version, and relationship in your production footprint.
In practice, a software digital twin:
-
Ingests build-time data like SBOMs (Software Bill of Materials).
-
Connects that data to deployment events and runtime states.
-
Maintains a continuously updated model of what’s actually running.
-
This live model becomes the authoritative source for detecting vulnerabilities, misconfigurations, and risk exposures — without agents, invasive scanning, or manual reconciliation.
Why Digital Twins Matter for Platform Engineering
Traditional DevSecOps pipelines and automation workflows provide strong checks before software is shipped, but once the code hits production, visibility often fades. Vulnerabilities are disclosed daily, most after deployment, and static scanning alone can’t keep up.
-
A digital twin changes this by giving security and platform teams:
-
Real-time awareness of every deployed component and its security posture.
-
Continuous vulnerability detection against known CVEs.
-
Automated remediation guidance tied to live system context.
-
An auditable evidence trail for compliance and reporting.
Because the twin lives outside the live environment, it provides real-time security intelligence with zero disruption to production systems — no agents, no rescans, no performance overhead.
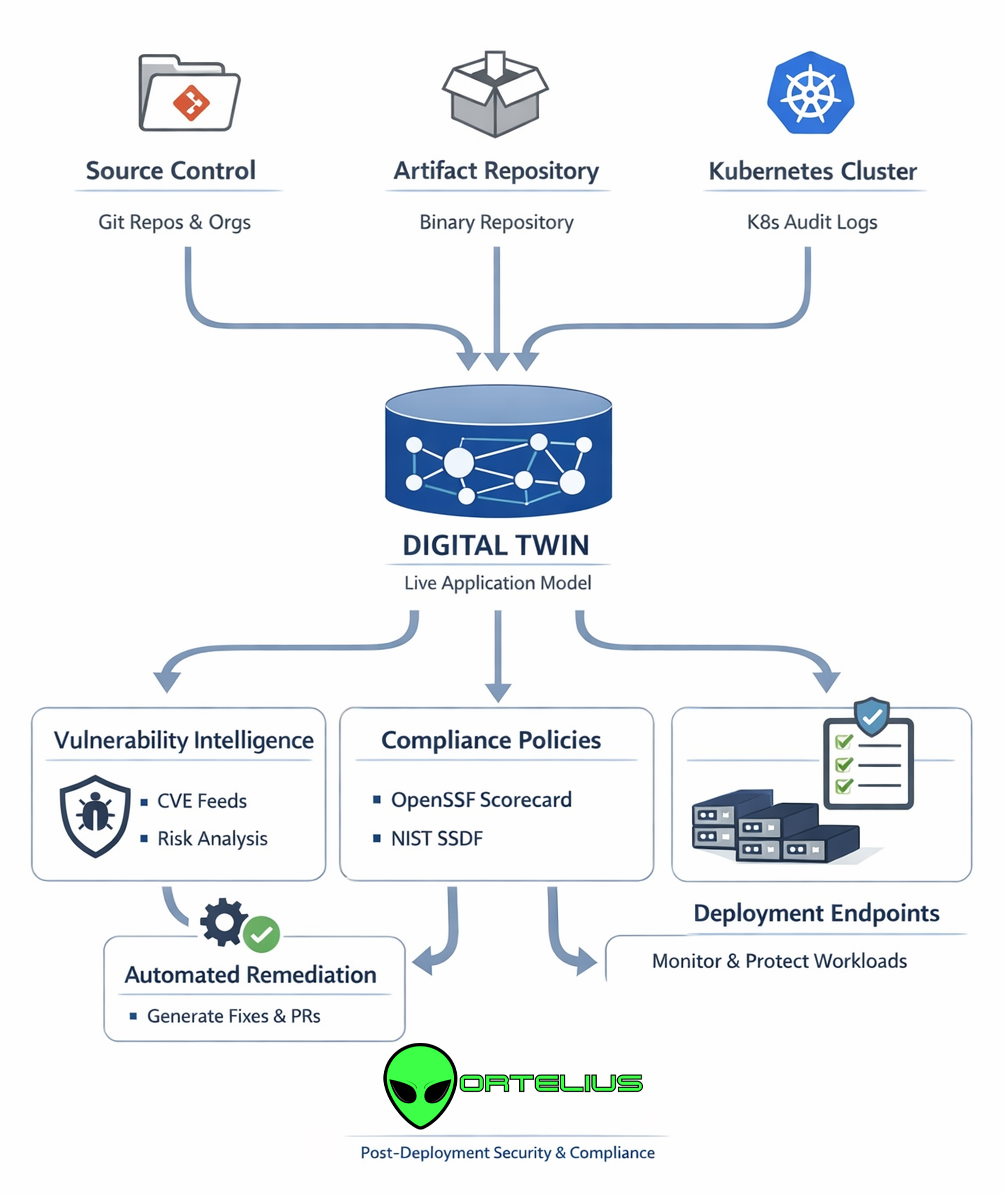
How Ortelius Builds the Digital Twin
Ortelius creates a deployment-aware digital twin by correlating data across the software lifecycle:
-
SBOM-Driven Inventory - Ortelius ingests SBOMs and dependency metadata generated during build and packaging, forming the foundation of the twin.
-
Deployment Intelligence - Deployments, environments, clusters, and endpoints are mapped to specific artifact versions — creating a precise “what’s running where” model.
-
Continuous CVE Correlation - The twin continuously synchronizes with vulnerability intelligence sources to detect when newly disclosed CVEs impact live systems.
-
Historical Evidence & Trends
From Visibility to Faster Remediation
A digital twin is only valuable if it drives action. With Ortelius, teams can:
-
Instantly identify which deployments are exposed
-
Prioritize fixes based on real attack surface
-
Reduce false positives by eliminating “not deployed” findings
-
Shorten MTTR for critical and high-risk CVEs — often to days instead of months
By grounding security decisions in live deployment context, remediation becomes targeted, measurable, and repeatable.
Digital Twins and the Future of Secure Software
As software environments become more ephemeral and complex, digital twins will evolve beyond visibility tools into self-defending systems — where automated intelligence continuously monitors, detects, and mitigates threats in real time. In the context of the Ortelius open-source ecosystem, this means pairing twin-based visibility with community-driven tooling that integrates seamlessly with your CI/CD workflows, SBOM pipelines, and vulnerability intelligence sources.
Join the Conversation & Contribute
Ortelius exists because of the open source community: from dependency topology modeling to vulnerability workflows that shape how teams think about post-deployment defense. If you’re interested in runtime vulnerability management, active risk prioritization, or tooling that surfaces real-world attack surface insight, we invite you to:
- Try Ortelius on GitHub and contribute features
- Open issues or PRs around runtime risk signals you care about
- Join the community calls to discuss vulnerabilities, attacker models, and remediation workflows
Security is a shared challenge, and open collaboration is how we level up the ecosystem together.