Identify and Neutralize Post-Deployment Threats
Ortelius Maps CVEs to Endpoints to Expose the Threat Landscape
Post-Deployment Vulnerability Control Plane for Fast Detection and Remediation
Control Threats Running Across the Live Attack Surface
Take command of your post-deployment vulnerability defense strategy. Ortelius guarantees you maintain an ironclad, up-to-date inventory of all open-source components within your software supply chain, enabling rapid, tactical decisions regarding open-source deployment across your entire operational theater, from code to cloud.
Software security threats don’t stop after your software is built and deployed, so neither should our security assumptions. Traditional vulnerability tooling largely stops at build-time, leaving a visibility gap in what’s actually running in production. Ortelius is designed to close that gap by bringing real-time post-deployment visibility into runtime risk, empowering open source developers, platform engineers, and SecOps teams with actionable threat context for what’s truly running across environments.
Why Post-Deployment Vulnerability Awareness Matters for Open Source Projects
Open source components are everywhere, in libraries, frameworks, and runtimes that make modern software work. But vulnerabilities don’t arrive on schedule: many are disclosed after software ships, and scattered throughout production workloads. Without continuous insight into what’s running and connected, teams end up chasing false positives or overlooking critical exposures entirely. Ortelius brings deployment-accurate context to vulnerability management:
-
You can instantly see when a newly disclosed CVE actually affects a running service.
-
You no longer have to guess which workloads are impacted across clusters and environments.
-
You can prioritize based on live risk rather than scan results generated months earlier.
This mindset shift, from static, point-in-time scans to always-on threat awareness, helps project contributors focus on the highest-impact risks.
From Static Scanning to Continuous Runtime Context
Scan-first workflows (whether SCA, SAST, or DAST) are valuable inputs, but they don’t answer the question that matters most in production: What vulnerabilities are present in services right now?
Ortelius complements upstream tools by correlating newly disclosed vulnerabilities with real deployment topology. This runtime correlation answers:
-
Which workloads reference a vulnerable package.
-
What active services are reachable from an attacker’s perspective.
-
Where risk exists in the actual topology, not just in a project repo.
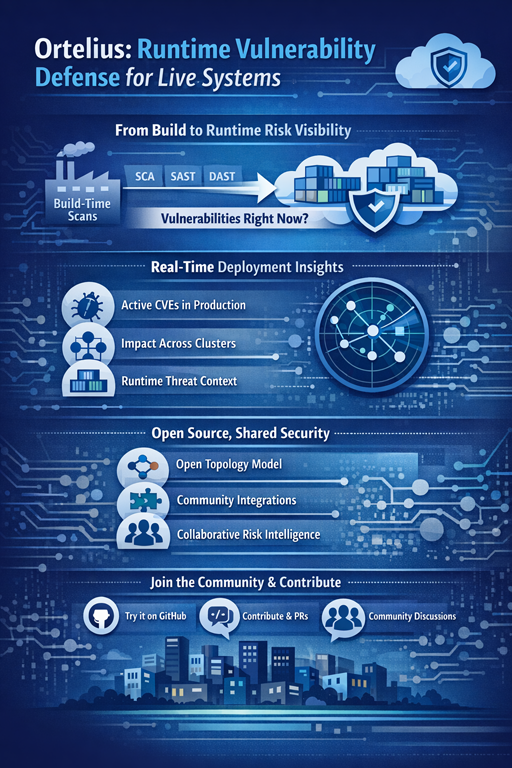
Shared Security Without Barriers
The open source community thrives on shared tooling and transparent workflows. Ortelius is built with that same spirit:
-
Open runtime topology model: Ortelius continuously tracks deployed services, containers, and dependencies without rescanning or intrusive agents.
-
Community-driven integrations: Connect vulnerability threat landscape, software bill of materials, and OSV.dev insights.
-
Collaborative risk intelligence: Developers, maintainers, and operators can all see and act on the same risk picture.
This approach aligns with emerging community best practices in supply chain security: shared awareness, reproducible insights, and tooling you can inspect and extend collaboratively.
How Ortelius Complements Upstream Security Engineering
Rather than replacing upstream best practices (like shifting left or embedding security in CI), Ortelius extends them across the full delivery-to-runtime lifecycle:
-
Upstream code and dependency scans feed into the runtime context.
-
Runtime risk signals improve prioritization for patch releases, dependency updates, and incident response.
-
Contributors and maintainers have a shared signal set to triage issues that matter in production.
Projects that adopt this posture not only strengthen their own quality and risk posture, but also contribute insight into the broader ecosystem, transforming raw scan data into collective situational awareness.
Join the Conversation & Contribute
Ortelius exists because of the open source community: from dependency topology modeling to vulnerability workflows that shape how teams think about post-deployment defense. If you’re interested in runtime vulnerability management, active risk prioritization, or tooling that surfaces real-world attack surface insight, we invite you to:
- Try Ortelius on GitHub and contribute features
- Open issues or PRs around runtime risk signals you care about
- Join the community calls to discuss vulnerabilities, attacker models, and remediation workflows