Ortelius Blog
Topics include Supply Chain Security, Vulnerability Management, Neat Tricks, and Contributor insights.
How to Bake an Ortelius Pi Part 4 | Cloudflare Certificates and Traefik
Introduction
In part 3, of this series we used the GitOps Methodology to deploy the Cert Manager, NFS CSI Driver for Kubernetes to connect to the Synology NAS for centralised dynamic volume storage, Metallb Load Balancer, Traefik Proxy as the entrypoint for our Microservices and Ortelius the ultimate evidence store using Gimlet as the UI to our GitOps controller Fluxcd.
In part 4 we will setup Cloudflare, LetsEncrypt and Traefik to secure incoming requests with certificates.
Cloudflare | Connectivity Cloud
You might know Cloudflare as a CDN but its so much more than that. Cloudflare is packed with amazing features and security offerings which are just to many to cover in this blog.
Cloudflare have kindly provided a free plan which we will use, so the first thing you need to do is set up an account for yourself or if you have an account login.
Buying a domain name
- Now we need a DNS domain so if you don’t have one you will need to buy one which you can do through Cloudflare.
- Click on
Websites
- Click on
Add a site
- Click on
register a new domain
- Click in the
Search for a domain namebox and find a domain
- Cloudflare will tell you if your domain is available. Unfortunately my cats name
mottles.comwas not available. She will not be impressed - Pick your domain and brandish your credit card
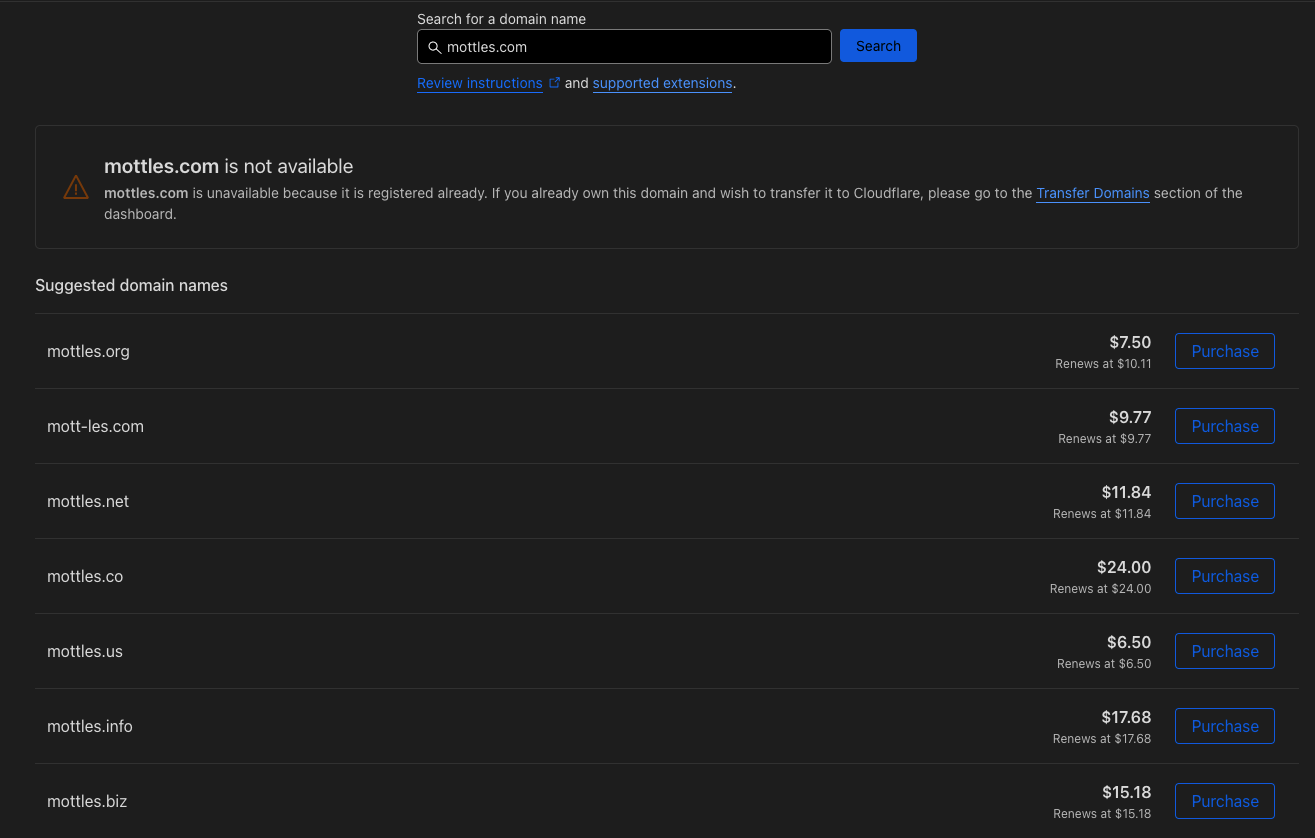
- At the end of the process when you get back to
Websitesyou should see your new domain registered - Here you can see my domain
pangarabbit.com - Click on our new domain and head over to
DNS

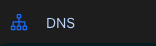
- You should have 2 DNS A records like below |
* is for wildcardand the domain apexpangarabbit.com - The domain apex record should be there but you might have to add the wildcard if memory serves me correctly
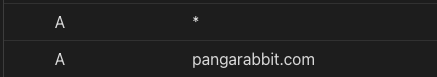
SSL/TLS
- Lets head over to
SSL/TLSnow

- You will be faced with the following screen and you want to have
Full (strict)enabled
- Below are some caveats to take note of which are taken from that little
Helpbutton
Why isn’t my site working over HTTPS?
Certificate provisioning typically takes around 15 minutes for paid plans and up to 24 hours for Free plans. Contact support if you do not have a certificate after that time. If the certificate is already “active” under the Edge Certificates tab, but you still cannot access your site over HTTPS, refer to the troubleshooting documentation. What encryption mode should I use?
Cloudflare strongly recommends using Full or Full (strict) modes to prevent malicious connections to your origin. For details on each available mode, refer to the encryption modes documentation.
- I turned this on
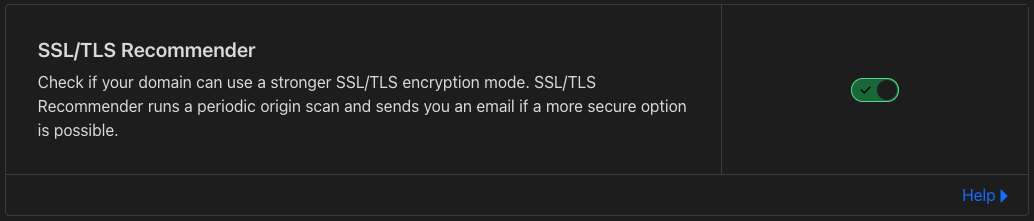
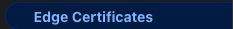
- Clicking on
Edge Certificatesyou will see that the kind folks at Cloudflare have provided you with a certificate for free also known asUniversal SSL
Attention: Let’s Encrypt’s chain of trust will be changing on September 2024. Universal SSL certificates will be automatically switched to a more compatible certificate authority. Review our documentation for details and to understand the impacts on other certificate types.

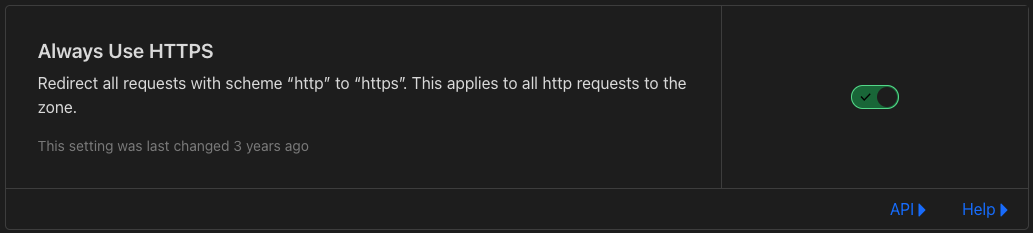
- Enable
Always Use HTTPS
- I set
Minimum TLS VersiontoTLS 1.3for the best security
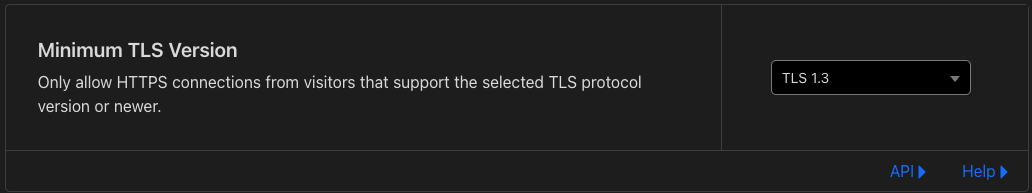
- I enabled
Opportunistic Encryption
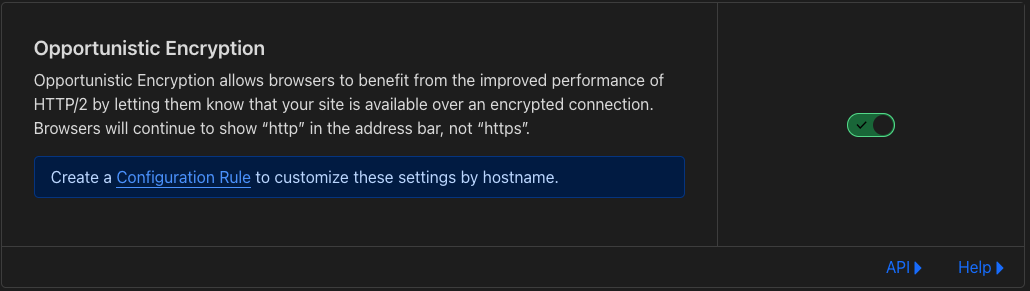
- I turned on
TLS 1.3for the best security
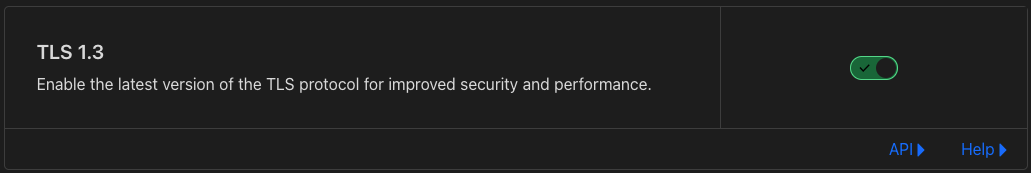
- I turned on
Automatic HTTPS Rewrites
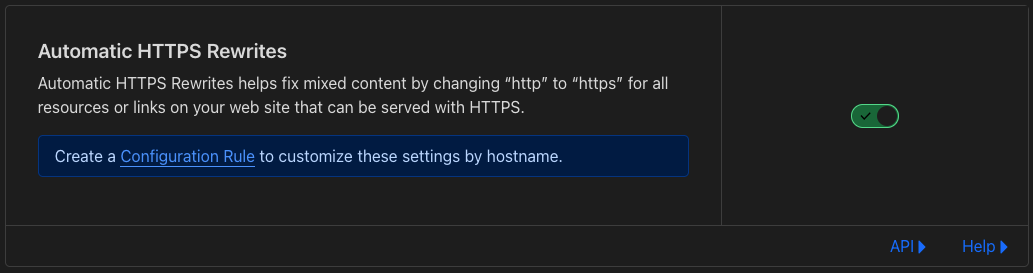
Great we should have a functional certificate which will be auto renewed and we can use Traefik as the single point of entry for secure connections.
Gimlet GitOps Infrastructure
Traefik
Helm-Release | Traefik
- Lets go back to our Traefik Helm Release and make some amendments
- Edit
traefik.yamlin thehelm-releasesdirectorygitops-<your name>-infrawhich was created by Gimlet and Fluxcd with the following changes
Manifest Folder | Traefik
- The folks at Traefik put this nice piece of logic in the Helm Chart that allows you to create a config file which is dynamically monitored by Traefik
- I am using this to manage the Lets Encrypt certicate renewal in conjunction with Cloudflare
- Its time to
ENABLEthe certificate logic in/manifests/traefik-dynamic-config.yamlandgit pushand allow Flux to handle the deployment
file:
# -- Create a file provider
enabled: true
# -- Allows Traefik to automatically watch for file changes
watch: true
# -- File content (YAML format, go template supported) (see https://doc.traefik.io/traefik/providers/file/)
# content:
providers:
file:
directory: /manifests/traefik-dynamic-config.yaml
-
The logic in the
traefik-dynamic-config.yamlwould have created asecretwith your Cloudflare API token and aIssuerfor your certificate usingCertificate Manager -
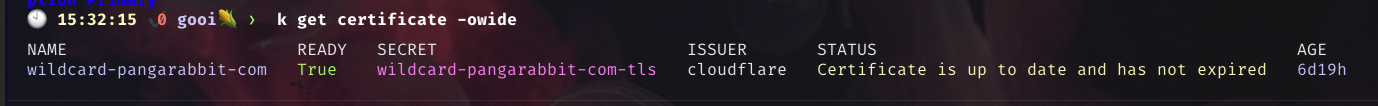
Run the following to see your created certificate
kubectl get certificates -owide -n infrastructure
- Mine is called
wildcard-pangarabbit-combut we are are interested in theSECRET
- Below I am showing the
ingressRoutefor the dashboard and you can see I only havewebsecureenabled now - I have added the
tlsconfiguration which matchesSECRETas in the above image
ingressRoute:
dashboard:
# -- Create an IngressRoute for the dashboard
enabled: true
# -- Additional ingressRoute annotations (e.g. for kubernetes.io/ingress.class)
annotations: {}
# -- Additional ingressRoute labels (e.g. for filtering IngressRoute by custom labels)
labels: {}
# -- The router match rule used for the dashboard ingressRoute
matchRule: Host(`traefik.pangarabbit.com`) #PathPrefix(`/dashboard`) || PathPrefix(`/api`)
# -- Specify the allowed entrypoints to use for the dashboard ingress route, (e.g. traefik, web, websecure).
# By default, it's using traefik entrypoint, which is not exposed.
# /!\ Do not expose your dashboard without any protection over the internet /!\
entryPoints: ["websecure"]
# -- Additional ingressRoute middlewares (e.g. for authentication)
middlewares: []
# -- TLS options (e.g. secret containing certificate)
tls:
default:
defaultCertificate:
secretName: wildcard-pangarabbit-com-tls
healthcheck:
# -- Create an IngressRoute for the healthcheck probe
enabled: false
# -- Additional ingressRoute annotations (e.g. for kubernetes.io/ingress.class)
annotations: {}
# -- Additional ingressRoute labels (e.g. for filtering IngressRoute by custom labels)
labels: {}
# -- The router match rule used for the healthcheck ingressRoute
matchRule: PathPrefix(`/ping`)
# -- Specify the allowed entrypoints to use for the healthcheck ingress route, (e.g. traefik, web, websecure).
# By default, it's using traefik entrypoint, which is not exposed.
entryPoints: ["traefik"]
# -- Additional ingressRoute middlewares (e.g. for authentication)
middlewares: []
# -- TLS options (e.g. secret containing certificate)
tls: {}
- To enable the certificate for all the workloads behind Traefik you need to change the following in your
Helm Releaseand make your certifcate the default
# -- TLS Store are created as [TLSStore CRDs](https://doc.traefik.io/traefik/https/tls/#default-certificate). This is useful if you want to set a default certificate. See EXAMPLE.md for details.
tlsStore:
default:
defaultCertificate:
secretName: wildcard-pangarabbit-com-tls
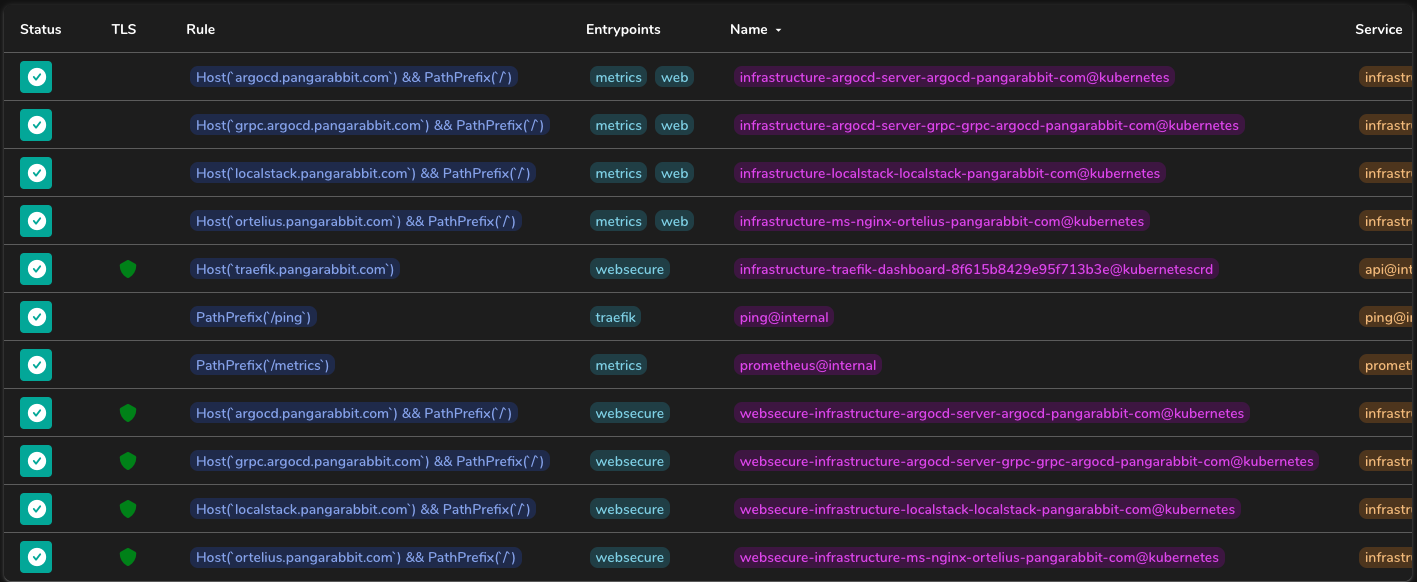
- In the following image we can see that our services have green shields to indicate that they are configured with
TLS - To access the Traefik dashboard the URL is
traefik.pangarabbit.com(Access your dashboard at your domain name)
All we have done now is secure the Traefik dashboard but how would we do it for other workloads. Lets look at a few examples.
Ortelius HTTPS
- For Ortelius we had to use the
k3dtype to make it Traefik aware - Now when requests arrive at Traefiks front door Traefik is aware of Ortelius and can send requests to
ms-nginxmicroservice and gain access to the Ortelius backend
ms-nginx:
ingress:
type: k3d # --set ms-nginx.ingress.type=k3d`
# This setting is for enabling the Traefik Class so that Traefik is made aware of Ortelius
# K3d https://k3d.io/v5.6.0/ is a lightweight Kubernetes deployment which uses Traefik as the default
dnsname: ortelius.pangarabbit.com # --set ms-nginx.ingress.dnsname=<your domain name goes here>
# The URL that will go in your browser to access the Ortelius frontend
Argocd HTTPS
- For Argocd I had to edit the
ingressClassNameto make it Traefik aware and also enableTLS
# Argo CD server ingress configuration
ingress:
# -- Enable an ingress resource for the Argo CD server
enabled: true
# -- Specific implementation for ingress controller. One of `generic`, `aws` or `gke`
## Additional configuration might be required in related configuration sections
controller: generic
# -- Additional ingress labels
labels: {}
# -- Additional ingress annotations
## Ref: https://argo-cd.readthedocs.io/en/stable/operator-manual/ingress/#option-1-ssl-passthrough
annotations:
{}
# nginx.ingress.kubernetes.io/force-ssl-redirect: "true"
# nginx.ingress.kubernetes.io/ssl-passthrough: "true"
# -- Defines which ingress controller will implement the resource
ingressClassName: "traefik"
# -- Argo CD server hostname
# @default -- `""` (defaults to global.domain)
hostname: "argocd.pangarabbit.com"
# -- The path to Argo CD server
path: /
# -- Ingress path type. One of `Exact`, `Prefix` or `ImplementationSpecific`
pathType: Prefix
# -- Enable TLS configuration for the hostname defined at `server.ingress.hostname`
## TLS certificate will be retrieved from a TLS secret `argocd-server-tls`
## You can create this secret via `certificate` or `certificateSecret` option
tls: true
FYI make sure you backup your persistent volumes on the NFS server
Conclusion
In Part 4 we configured a certificate for our domain using Cloudflare, LetsEncrypt and Traefik. From my experience the crucial configuration change for any workloads to access the frontend securely was to enable the ingress, TLS and to change the ingressClassName to traefik in the Helm Release values.
Happy alien hunting…….
Next Steps
How to Bake an Ortelius Pi | Part 5 | Ortelius Marries Jenkins
